Posted on: May 8, 2025
Evil Portal Demo on Flipper Zero: Why You Should Think Twice Before Connecting to Public WiFi
If you’ve ever hopped onto a random “Free Wi-Fi” network at a coffee shop, airport, or hotel, this post is for you!
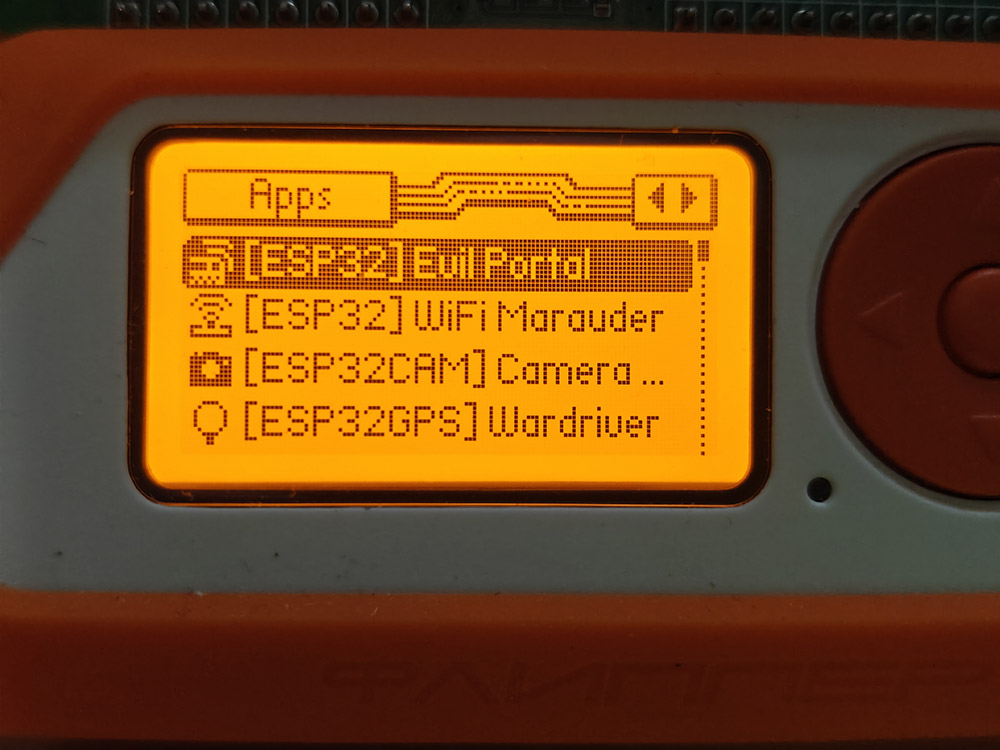
What I’m showing here isn’t new, and it’s definitely not a gimmick. It’s a demonstration using the Evil Portal script on a Flipper Zero with the WiFi developer board – just one of many ways someone can trick you into handing over your personal info without you ever realizing it.
This demo is meant to show exactly how that trick happens.
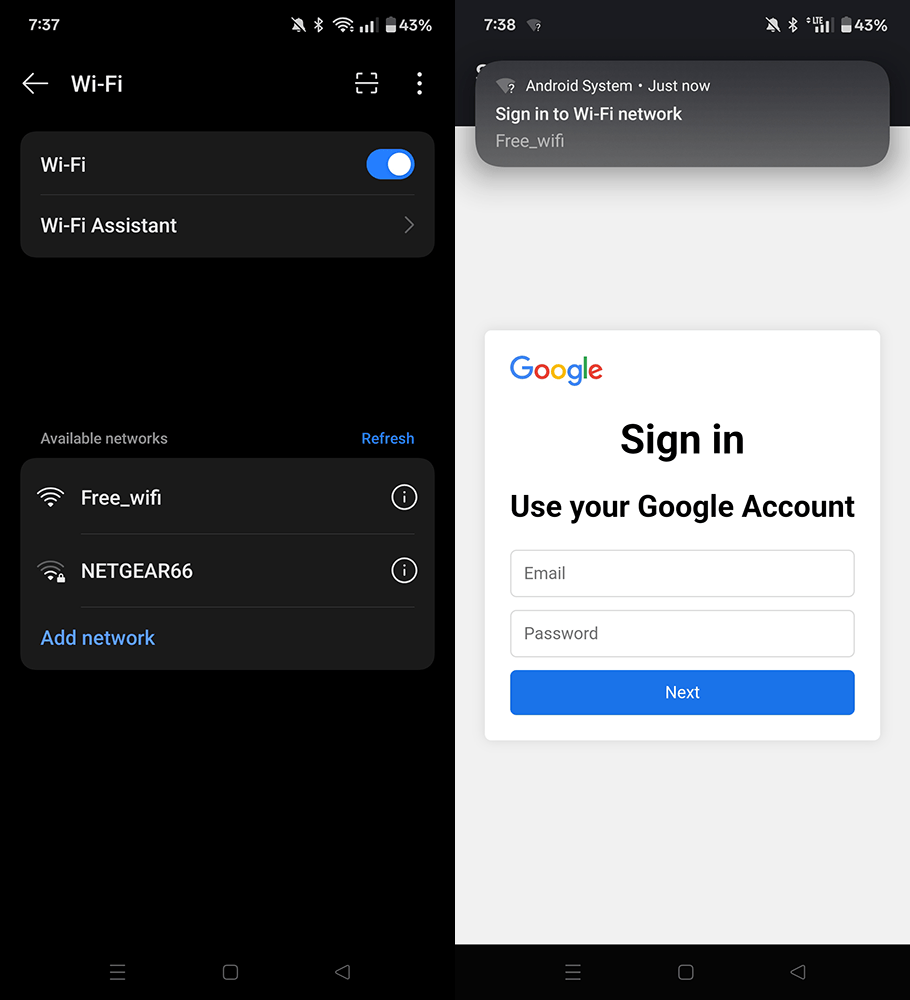
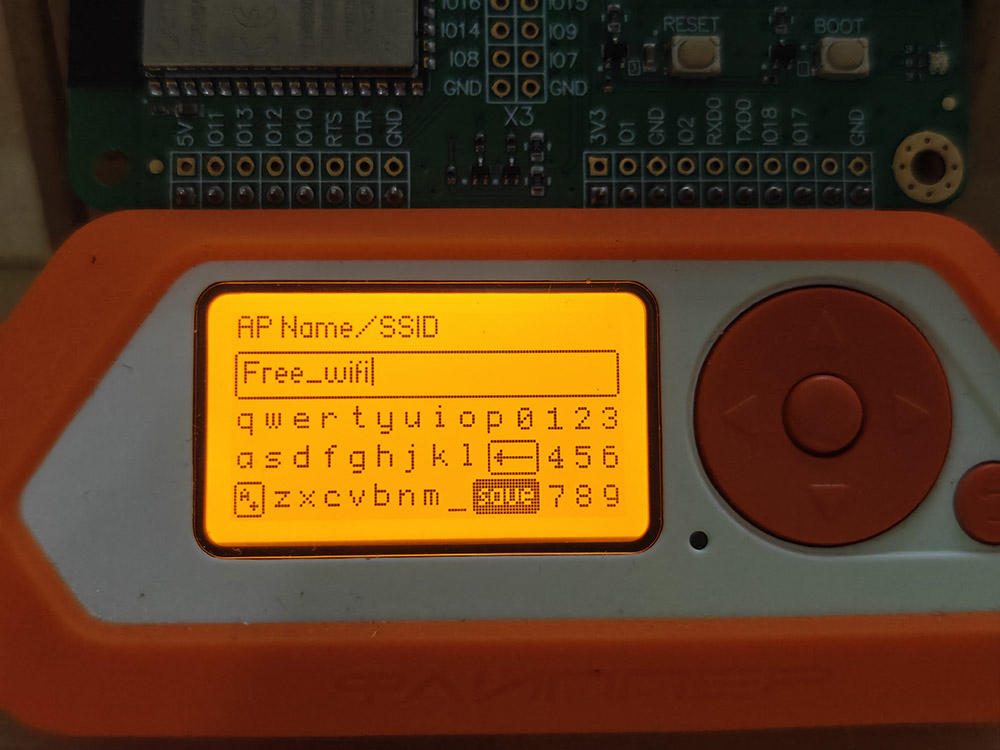
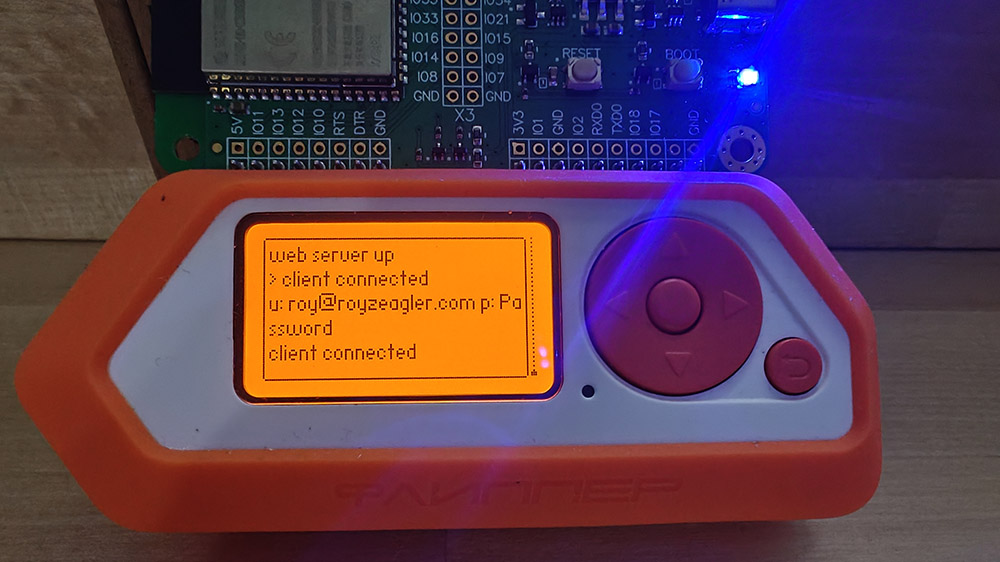
In the video, I create a fake WiFi network that looks like an open public hotspot. I named it Free_wifi, because that’s the exact kind of name someone might connect to without a second thought. Once a device connects, it gets redirected to a login screen that looks exactly like something you’d expect—Google, Facebook, or even your office VPN. It looks legit, but it’s not.
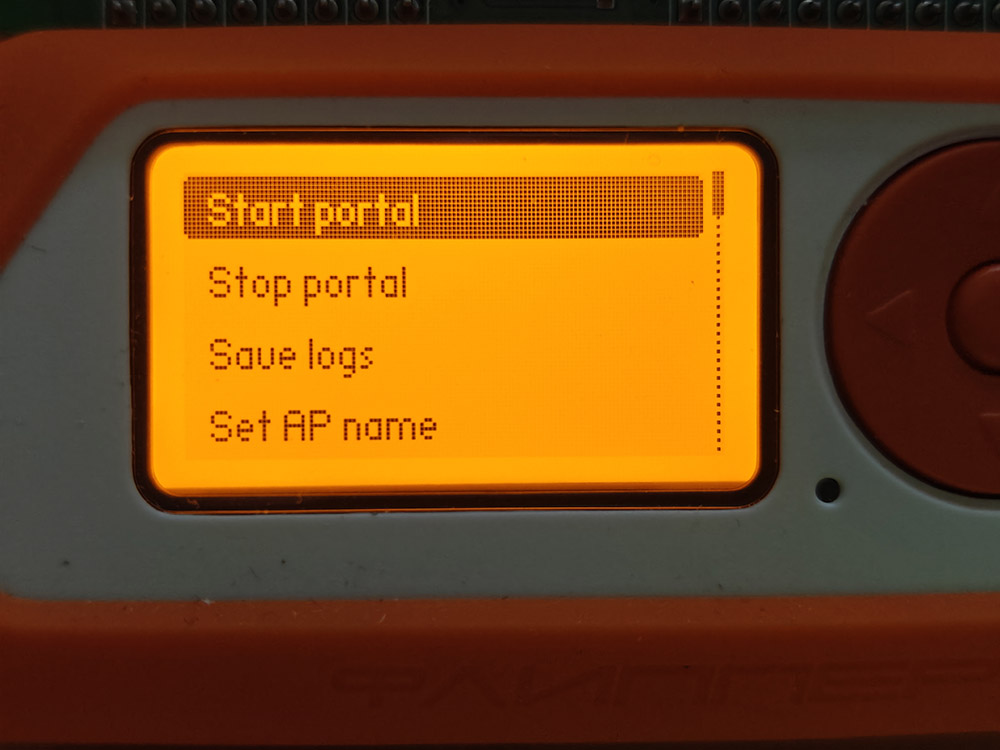
This kind of setup actually doesn’t require a laptop or any coding. Once the Wi-Fi board is connected, Evil Portal launches straight from the Flipper Zero’s interface. Scroll, click, and the whole thing is live within seconds. Broadcasting a professional looking login page that feels real to anyone who connects.
Anybody with a hundred bucks worth of gear could have Evil Portal up and running in less than 10 minutes. It’s quick, it’s easy, and honestly it’s a little alarming how convincing it can be.
To be clear, I’m not using this to prank people or steal anything. The purpose of the video and this post is to educate and spread awareness. Most people don’t realize that a network named Starbucks_WiFi could be completely fake. They see the name, click connect, and assume the popup asking for their email and password is part of the process.
The truth is, most hacks aren’t some high level, code heavy attack. A lot of them are just social engineering tricks that rely on people being a little too trusting in the moment.
And THAT is why it’s SO important to be careful when using public Wi-Fi! In fact, NEVER use public WiFi unless you just absolutely have to. If possible, always use your phone’s data instead. Yea, it might be a little slower, but man it’s so much safer! Oh, and if you do happen to find yourself on public WiFi and a login screen pops up unexpectedly – take a second to question it. Don’t enter anything sensitive unless you’re absolutely sure the network is legit.
If this demo does anything, I hope it shows how easy it is to create a convincing trap, and why you should NEVER assume public WiFi is safe just because it looks familiar.

Leave a Reply
You must be logged in to post a comment.